CISOs tell VentureBeat they’re looking to get more value from security operations (SecOps) by identifying threats rather than analyzing them after an event. Gartner’s direction is that “SecOps’ goal is to create proactive risk understanding and enable threat exposure reduction as well as detection of, and response to, cyber events that negatively affect the organization.”
SecOps teams need help to get out of a reactive approach of analyzing alerts and intrusion, breach and botnet events after they’ve occurred. As a first step to solving this challenge, enterprise security teams and the CISOs that lead them are pushing for greater real-time visibility. In addition, tech-stack consolidation, a strong focus on minimizing costs, and the need to stand up remote SecOps locations faster than on-premises systems and their infrastructure allow are driving SecOps teams’ need for threat intelligence and more real-time data.
Improving SecOps with real-time threat intelligence
For SecOps to deliver on its potential, it must start by reducing false positives, filtering out inbound noise, and providing threat intelligence that triggers automated detection and remediation actions. In short, SecOps teams need threat intelligence providers to interpret and act on inbound packets immediately, finding new ways to capitalize on real-time data. Fortunately, the next generation of threat intelligence solutions is purpose-built to provide post-attack analytics, including forensic visibility across all events.
The National Institute of Standards and Technology (NIST) defines threat intelligence as “threat information that has been aggregated, transformed, analyzed, interpreted, or enriched to provide the necessary context for decision-making processes.” NIST mentions threat intelligence in their NIST SP 1800-21, NIST SP 800-150, and NIST SP 800-172A standards.
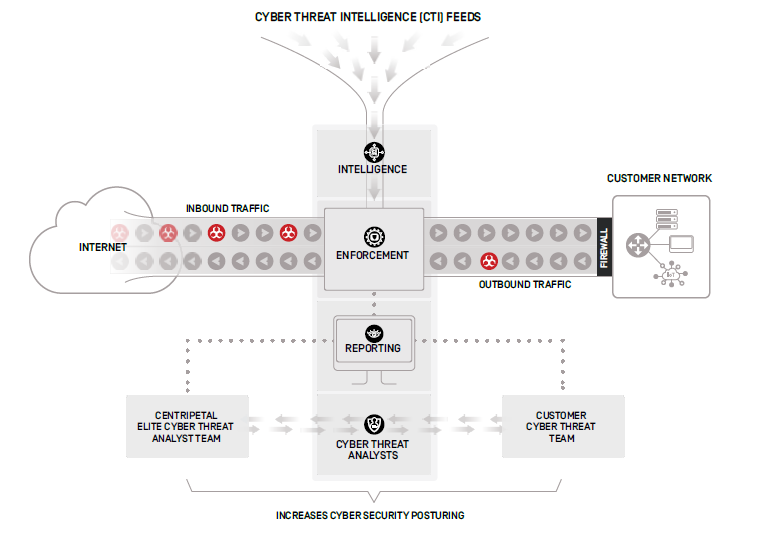
Leading vendors include Centripetal, whose CleanINTERNET solution operationalizes cyberthreat intelligence at scale by combining automated shielding, advanced threat detection (ATD) and dedicated teams of human threat analysts. Centripetal’s customer base includes government agencies, financial institutions, healthcare providers and critical infrastructure providers.
“Threat intelligence, if you apply it properly, can become a highly effective tool to determine automatically who should come into your network and who should not, and thus gives an organization risk-based control,” said Centripetal’s CEO, Steven Rogers.
There are more than 75 vendors in the threat intelligence market today, including CrowdStrike, Egnyte, Ivanti, Mandiant, Palo Alto Networks, and Splunk. All strive to strengthen their threat intelligence as core to their ability to contribute to their customers’ SecOps needs.
Centripetal’s architecture is noteworthy in its use of artificial intelligence (AI) and proprietary algorithms to aggregate, filter, correlate, detect, triage and analyze thousands of global feeds at massive scale and machine speed. AI acts as an orchestration technology in their platform, coordinating threat intelligence feeds and enforcement algorithms and simultaneously reporting to both Centripetal’s internal cyberthreat analyst team and that of the customer.
Scaling threat intelligence in the enterprise
VentureBeat recently sat down virtually with Chuck Veth, president of CVM, Inc., to learn how enterprises are putting threat intelligence to work and how his firm helps their implementations scale. CVM, an IT services firm with more than 30 years of experience, is a two-time winner of Deloitte’s CT Fast 50. Chuck’s firm implements and supports Centripetal and is a leading reseller to enterprise and government accounts. Presented here are selected segments of VentureBeat’s interview with Chuck:
VentureBeat: What challenges do your customers face that led you to contact Centripetal to be a reseller for them?
Chuck Veth: “The challenge to enhance cybersecurity is constant. We first learned about Centripetal from one of our accounts. After evaluating it and presenting it to our customers, we realized that the CleanINTERNET service is an excellent final layer of security for public-facing networks. We look at it as a necessary insurance policy. When you turn on CleanINTERNET, it gets used thousands of times a minute.”
VB: Keeping with the insurance analogy, can you expand on how you see the value Centripetal provides?
Veth: “It’s not like car insurance; you can do the math easily on asset protection insurance. It’s more like the car insurance component that covers damage to the occupants, which you typically don’t think about when you’re evaluating car insurance. You’re thinking about your car. But the truth is, car insurance is really there for the people because they’re irreplaceable. When thinking about network security, you mainly approach it from the packet inspection perspective. Centripetal’s CleanINTERNET service works from a completely different perspective. It is determining if the remote IP address is a threat actor; if it is, it blocks it. You need to use this perspective as well; the cost of missing a threat actor can close your business.”
VB: What are some of the most valuable lessons learned regarding how Centripetal provides greater threat intelligence of your shared customers with them?
Veth: “One of the most exciting outcomes of having the Centripetal CleanINTERNET service is its ability to separate a threat actor from a non-threat actor on some very common pathways of the internet. HTTPS traffic travels on port 443, HTTP on port 80, and email travels on port 25, et cetera. Years ago, when some services lived on relatively unique ports, they were easy to monitor for an attack. Today it’s harder as the industry has moved to a world that lives on a handful of ports, like 443, using SSL certificates.
“For example, individuals on private networks often turn to public proxy server websites to avoid corporate filtering, such as blocking day trading. The user connects to the proxy service, and it connects their browser to the day trading site. All the user needs to do is find a proxy service that is not blocked by their company firewall. Bad actors often operate these proxy services as they can track every detail of the online activity.”
VB: That’s the danger of using a proxy service that isn’t verified to visit a site your company has blocked. How does threat intelligence help identify the threat and protect infrastructure?
Veth: “Centripetal is looking at the IP address and saying, ‘I have a list of billions of IP addresses that are known to be operated by threat actors.’ It’s a different way of looking at things. And, to do it correctly, Centripetal compiles real-time information from hundreds upon hundreds, even thousands, of threat intelligence feeds. And that’s the secret sauce of the Centripetal CleanINTERNET service. They are normalizing the data from thousands of real-time threat intelligence feeds to say, ‘Hey, this particular site popped up in three or four different threat intelligence databases. And for us, that is a sign that it is a threat actor. And so, we’re going to block it.’”
VB: What’s your favorite example of how effective Centripetal is at uncovering bad actors’ attack strategies that are cloaked to avoid detection?
Veth: “One day, we got a note from our Centripetal security analyst, ‘…this threat actor’s trying to communicate with this customer – it’s a known threat actor operating out of Europe – it’s this IP address….’ We’re an IT firm, so we looked up the IP address, and the IP address was at a hosting facility in New York.
“And we’re like, ‘What? Why did our security analyst tell us that this IP address was in this foreign country when one of our staff found that it’s in New York?’ We browsed to the IP address. It was a hosting company in New York that only takes payment via cryptocurrency and requires no audit to host on its service. So any host can sign up for this service with no authentication. But the Centripetal device knew that this site, although hosted in New York, was a threat actor from a foreign country. This would have never been blocked by geofiltering, but the Centripetal service was able to identify it and block it.”
How threat intelligence enables zero trust
Having threat intelligence add value in a zero-trust framework requires identifying and classifying threats before they gain access to a corporate network. Interpreting every data packet and then evaluating its level of risk or trust is essential — while factoring in and correlating to all known global threat feeds in an adaptive, customizable service. Identifying and classifying threats before they reach the network is core to the future of threat intelligence and the ability for SecOps to migrate to a zero-trust framework.
Threat intelligence needs to do the following to increase its value to zero-trust initiatives:
Enforce zero trust by inspecting every packet of bidirectional traffic
Vendors are setting service goals that center on their ability to shield their customers’ organizations from all known attacks. Each of the competing vendors in threat intelligence is taking a different approach.
Continually improve the real-time visibility across the known threatscape
Most threat intelligence vendors are more focused on analyzing the data from previous events. A few have proven exceptional in using machine learning algorithms to look at predictive patterns in traffic and attack data. What’s needed is a threat intelligence system that can aggregate the data of every inbound packet, then correlate the analysis results with known threats. Centripetal compares each packet’s contents to all available cyberthreat indicators in real time, using thousands of global threat feeds to support their single, fully managed service.
Reduce false positives, inaccurate alerts and events by verifying every access attempt before it gets inside the corporate network
A core tenant of zero trust is to assume the network has already been breached and the attacker needs to be contained so they can’t laterally move into core systems and do damage. Leading threat intelligence system providers are applying machine learning algorithms to reduce the noise from external networks, filtering out extraneous data to find the actual threats. Besides contributing to the zero-trust initiatives of an organization, it helps reduce the burden on the security operations center (SOC) in having to clear false positives and alerts.
SecOps must improve at delivering business-driven outcomes based on real-time data insights, learning to be more adaptive and quicker to respond at scale. As part of the next generation of threat intelligence solutions, companies like Centripetal support SecOps teams by specializing in providing threat intelligence to reduce false positives, filter out inbound noise and trigger automated detection and remediation actions.
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative enterprise technology and transact. Discover our Briefings.

